A five-step Lifecycle Management Framework for Physical Security Systems.
Table of Contents
- What is Physical Security Lifecycle Management?
- Operational lifecycle management
- Step 1: Plan
- Step 2: Design
- Step 3: Install
- Step 4: Maintain
- Step 5: Audit
- Streamlining Physical Security Lifecycle Management
Regardless of their specialty, security professionals recognize physical security is the first layer of protection against any physical or digital threat. Over 85% of cyber security breaches in the past few years involved a human element which only highlights importance physical security. Physical is broad field with many facets that must be managed to ensure an At its involves measures directly applicable protecting and infrastructure. Lifecycle management often but part systems constantly monitored maintained they function as intended provide level protection required by organization. Chief Security Officers Professionals decision-makers are challenged balancing needs organization budgetary requirements implement maintain system. The challenge for budgets reactionary not viewed critical component budget. This major system failure can have significant financial impact on mission empower professionals data tools needed help them manage their rel=”noopener”>physical security systems. If you’re a CSO, PSP, or system owner looking to strengthen your physical security and streamline your lifecycle management program, this article will show you how.
What is Physical Security Lifecycle Management?
Physical security lifecycle management is the process of planning, implementing, maintaining, and upgrading physical security measures to protect an organization’s assets and personnel. This includes assessing risks, designing security systems, implementing controls, monitoring and testing the systems, and continuously improving the security posture.
The goal of physical security lifecycle management is to ensure that an organization’s physical security measures are effective, efficient, and aligned with the organization’s overall security strategy.
Some of the challenges impacting both the effectiveness of security systems and the focus of enterprise security teams are:
- Incomplete system information – not knowing what you have.
- Lack of visibility across the age of the components of the security system.
- Inconsistent tools to manage ongoing service and installation quality.
- Difficulty identifying trends in physical security systems.
- Lack of standardized processes and procedures.
Without a well-defined lifecycle management process in place, security teams are left with no way to know the full lifecycle of their security systems or even if they are working correctly.
Operational lifecycle management
When it comes to lifecycle management, most physical security professionals and system owners focus on two main factors:
- Device functional lifetime: How long the device or system will operate before it is no longer useful and needs to be replaced.
- Economic lifecycle: How long a device or system will be effective before it is no longer cost-effective.
Operational lifecycle management is the process of identifying, planning, and managing changes to physical security systems throughout the system’s lifecycle. A typical physical security system is composed of a series of interconnected subsystems whose lifecycles may range from a few years to decades or more. In the course of its lifetime, a physical security system will be modified to accommodate changes in the security mission and threats to the system. The modification process may occur in response to a threat, an upgrade to the physical security system, or a shift in security priorities..
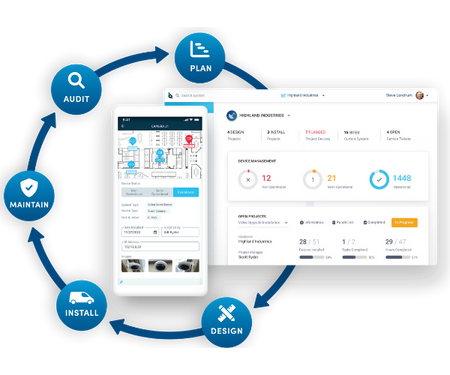
A well-defined physical security lifecycle management process should include an understanding of the physical security system lifecycle and address the following areas: Planning, Designing, Installation, Maintenance, and Auditing.
The Physical Security Lifecycle Framework
Establishing and maintaining a robust, physical security lifecycle management practice is challenging, but breaking it down and taking it one step at a time will make it more manageable.
This 5-step Physical Security Lifecycle Management framework is an effective way to keep things humming and make fiscally responsible security investments. This is a cyclical process that, when adopted well, drives continuous improvement.
Step 1: Plan
Planning is the process of assessing and identifying your organization’s security requirements and then building a solid plan to help your team meet them. Planning includes
- Determining people, environment and assets that need protecting.
- Understanding any regulatory requirements your security system must comply with.
- Inventorying your current physical security devices in your infrastructure, their lifespan, warranty status, service history and other information.
- Reviewing any recent security audit outcomes (See Step 5) to determine gaps.
- Building a strategy and budget for closing the gap between what you have and what you need.
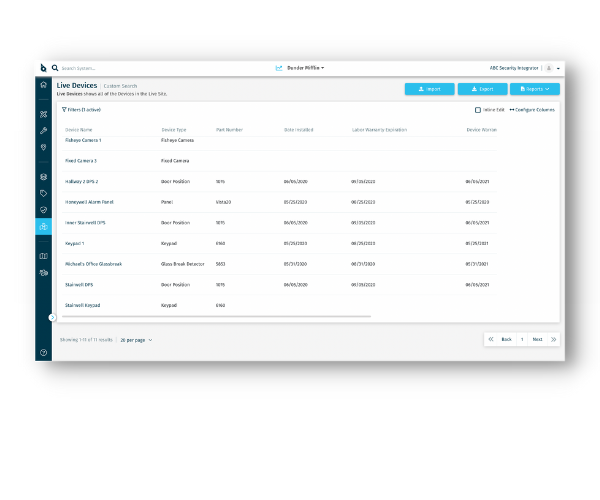
The Challenge:
In the planning stage, the most important thing enterprise security teams need is visibility – knowing where each device is, who installed it, when it was installed, what its current operating status is, how many times the device has failed and over what period of time.
Unfortunately, this is also where they struggle. Very rarely is all this information easy to locate and up-to-date, and when it is, it is stored in excel spreadsheets, CAD Drawings, paper-based floorplans and other disparate systems that don’t talk to each other.
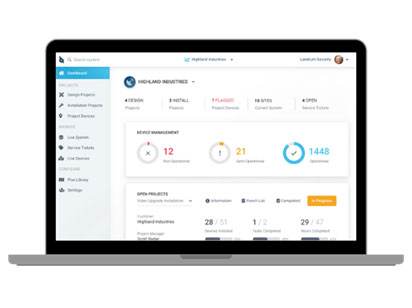
Adopting a comprehensive physical security lifecycle management platform like SiteOwl gives security teams and their vendors visibility at a very granular level, making the process of planning easier.
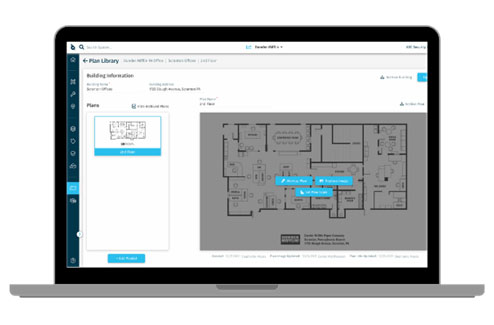
Step 2: Design
Designing is a multi-stage process using the information gathered in the planning step to build a security solution that the organization needs. Enterprise security teams often do this in partnership with their security integrators, consultants and other vendors.
As an organization expands, so does the number of physical assets it has. New locations, equipment, and buildings are common to any growing company. Still, as the number of connected devices continues to grow, the design process must take into consideration the following:
- The number of systems your organization has (e.g Video Surveillance, Access Control, Intrusion Detection, Critical Communication and other technologies).
- What is best suited for the environment and organization’s needs?
- What is needed to ensure they work together effectively?
- Whether they comply with any applicable laws and regulations.
- How well the system design aligns with the overall security strategy.
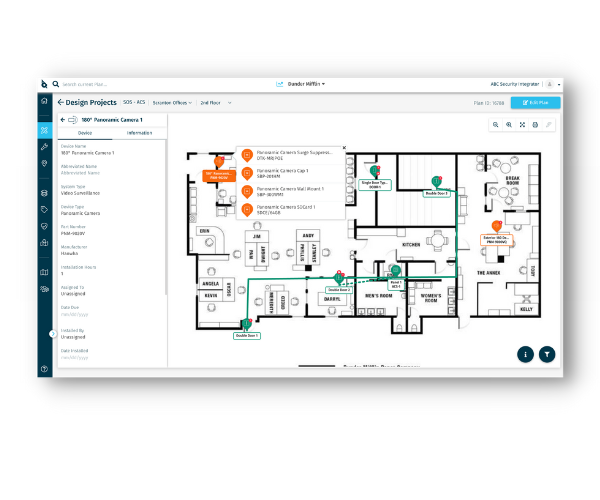
At an overly simplistic, but fundamental level, a robust security design is one that does an effective job of protecting people, assets and environments, is cost effective, and will last a while without needing a complete overhaul.
The Challenge:
Design is meant to be a collaborative process, but most design tools teams use aren’t geared for real-time collaboration. The number of times design files go back and forth before being approved can cost security teams extra time, effort and money.
SiteOwl allows security teams to bring their integrators, consultants and other teams into a single design interface for real-time collaborative design, reducing sign-off time from days to hours.
Step 3: Install
When installing a new physical security system or upgrading an existing one, there are a number of decisions that must be made. For instance
- Should the organization work with a security integrator to install the system or self-install?
- Who will manage the project?
- How will progress be reported?
- Who will sign off?
- How will the quality of work be evaluated?
- How will the team ensure that the project is completed on time and under budget?
At an overly simplistic, but fundamental level, a robust security design is one that does an effective job of protecting people, assets and environments, is cost effective, and will last a while without needing a complete overhaul.
The Challenge:
At this stage of the lifecycle, communication is key. Often, these projects involve multiple teams across multiple locations. Project managers have the unenviable task of staying on top of progress at every location but don’t always get information back from the field when they need it. Additionally, many organizations and security integrators turn to excel spreadsheets or other generic project management systems that aren’t purpose built for physical security.
The result? Projects don’t finish on time, cost more, and no one really knows what is happening.
SiteOwl’s purpose-built mobile apps allow field installation teams to report progress, provide quality control images of installation work, and flag blockers in real-time, driving accountability.
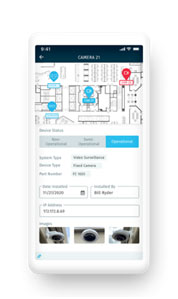
Step 4: Maintain
Physical security systems such as video surveillance, access control and intrusion detection require regular maintenance. This helps security teams keep their systems up to date and plan for repairs or replacements, and reduce the likelihood of a security event that resulted from faulty or malfunctioning equipment.
Maintenance includes activities such as
- Cleaning and refocusing lenses, housing and verifying camera placements.
- Inspecting power supply and network connections.
- Checking wiring and cable harnesses for wear and tear.
- Cleaning of control components and ensuring control equipment is operational.
- Updating firmware and software.
- Testing alarms and communication systems
- Reporting any anomalies or variations.
This is by no means an exhaustive list and each system type has its own set of tasks for preventive maintenance.
The Challenge:
Unfortunately, physical security systems don’t get the maintenance they need. And more often than they should, security incidents can be traced back to device failures regular maintenance could have prevented. When enterprise security teams don’t have a complete and centralized inventory of their security devices, it’s difficult to keep track of device failures, service ticket status, and preventive maintenance schedules.
SiteOwl helps security teams and their integrators to track and maintain key information video surveillance, access control, intrusion detection, critical communications, fire and life safety and many other system assets together into one platform. Preventive maintenance history, service ticket status, moves, adds and changes, device failure histories are all available on digital floorplans, accessible anywhere and at any time.
Step 5: Audit
Auditing is a crucial part of physical security lifecycle management, and it allows security teams to ascertain if current security systems and measures are fit-for-purpose.
Physical security systems audits help organizations assess and evaluate the current state of their physical security infrastructure as well as:
- Identify security gaps and loopholes in the current physical security infrastructure.
- Present suggestions for improvements or solutions to address identified gaps.
- Assess the level of effective compliance with physical security standards and regulations.
- Identify systems that may need to be retired or replaced.
- Provide the information needed to plan and budget for security investments.
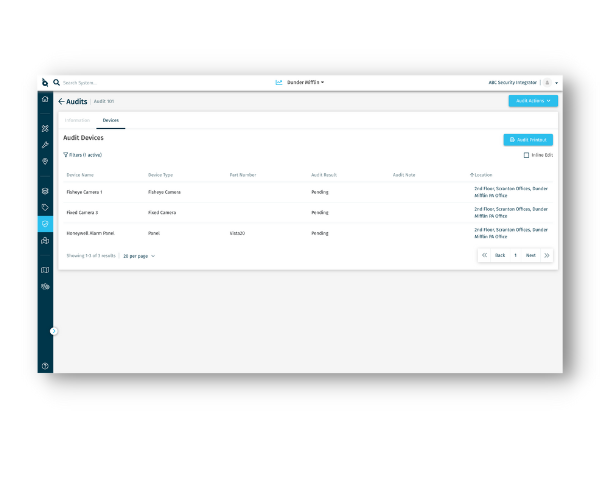
The Challenge:
At this stage of the lifecycle, organizations need actionable intelligence. When organizations have poor audit practices, it impacts their ability to make fiscally responsible security investments. The mechanics of compiling information from a security audit, including collating and analyzing data is a manual process. Considering how much of this data is stored in disparate systems, it’s no wonder that security teams struggle to establish strong lifecycle management practices.
SiteOwl tracks design, installation, maintenance and audit information in one place so security teams, their vendors and other teams have the right information at all times.

Streamlining Physical Security Lifecycle Management
Physical Security Lifecycle Management is not a one-time event. It is a cyclical process where information gathered in one step serves as an input for the next step. It begins when a security system is installed and continues until it is decommissioned. Security teams must constantly learn, adjust, improve and adopt best practices to meet the ever-changing security needs of the organization in today’s fast-paced digital environment.
Whether your organization has a robust physical security program in place or you are just getting started, implementing the lifecycle principles discussed in this article will provide a solid foundation for improving and strengthening your organization’s physical security posture.
Approaching your organization’s security posture from a lifecycle perspective can be daunting. With the right tools, resources, and processes, organizations can stay ahead of evolving threats and keep their systems secure and compliant.
Physical Security Lifecycle Management with SiteOwl
SiteOwl brings enterprise security teams and their security vendors together into one platform, driving visibility, collaboration and effectiveness. With SiteOwl, teams users can easily:
- Track and manage all physical security system devices across multiple locations from a single interface.
- Collaborate directly with internal and external security teams their integrator on new system designs, manage repairs and maintenance requests.
- Conduct system-wide audits to identify and repair security gaps.
- Keep track of key information such as warranties, installation dates, device connections, cable pathways and many other attributes.
Learn more about physical security lifecycle management and the benefits of leveraging technology to manage your physical security systems by downloading our free ebook, The Practical Guide to Managing Physical Security Systems.

Su Subburaj
Su is SiteOwl's CMO and leads all marketing and communications. Su has extensive strategy and management consulting experience and previously consulted for 3Sixty Integrated where she gained an in-depth understanding of digital transformation challenges in the physical security industry. When not working on strategies to expand SiteOwl's footprint, Su enjoys bad karaoke, weightlifting and traveling.




